SSH Tunnel
Good practice suggests that we should secure and encrypt the mavlink (APM Planner) connection from the GCS to the RPi. This can be easily accomplished without any additional code and is built into SSH.
Be aware that this is a TCP connection, so if you loose connection between the GCS and RPi, you will have to re-connect the APM Planner to establish the session.
RPi
Here is a simple way to secure communications.
I execute the APM binary on the RPi with the follwing command:
sudo ArduCopter-quad -A tcp:127.0.0.1:9999 -C /dev/ttyAMA0
This will setup a mavlink TCP connection listening on localhost (the localhost of the Rpi) on port 9999
GCS
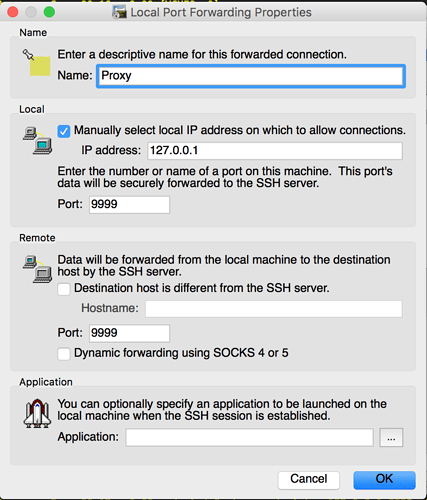
The next step is to SSH using your favorite SSH program that has port forwarding capabilities, I use SecureCRT but I also believe Putty supports port forwarding.
You should configure your SSH program to port forward from 127.0.0.1:9999 to the remote address 127.0.0.1:9999
Make the SSH connection to your RPi (you will have to know the IP address of your RPi) using the configured SSH connection above and leave the SSH window open (this is your SSH Tunnel, DO NOT close this connection or you will close your tunneled connection)
APM on GCS
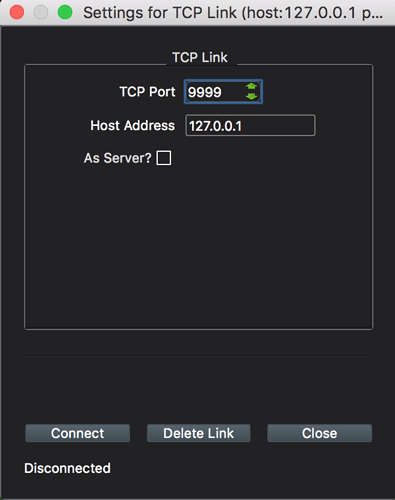
Fire up APM Mission Planner and create a TCP connection with the IP address: 127.0.0.1 with port: 9999 as shown below.
Connect
Connect and you should now have a SSH secure tunnel to your RPi with mavlink and APM Planner running through the tunnel.
Conclusion
Hope this helps some people out who want to secure their communications to their RPi. I use this method quite a lot for maintenance of production servers. The method described above only exposes the SSH port (usually port 22) to the outside world and only allow authorized users to connect to local services provided by the linux server/RPi.
Dale